Create And Enable A Screened Subnet Dmz
Designing and using dmz networks to protect internet servers Dmz screened subnet firewall architecture network two zone trusted untrusted demilitarized between routers creating additional set tag resize How to setup dmz demilitarized zone on a home router by tp link router
/28 subnet on DMZ | Netgate Forum
Screened subnet dmz Dmz subnet netgate forum helps trying wrong went hope figure where Screened dmz perimetral seguridad subnets
Dmz ip handbook examples
Dmz router tp link demilitarized zoneSubnet screened dns architecture dmz mail network internal ppt powerpoint presentation external Screened subnetScreened dmz subnet they.
/28 subnet on dmzScreened subnet architectures (building internet firewalls, 2nd edition) Dmz subnet servers internet architectures networks using linuxjournal protect designing breeze flapping figureScreened subnet architecture routers two using figure firewalls architectures.

Chapter 13. example configurations
.
.


PPT - Seguridad Perimetral PowerPoint Presentation, free download - ID

PPT - Chapter 10 PowerPoint Presentation, free download - ID:2760009

PPT - Chapter 10 PowerPoint Presentation, free download - ID:2760009

Chapter 13. Example Configurations
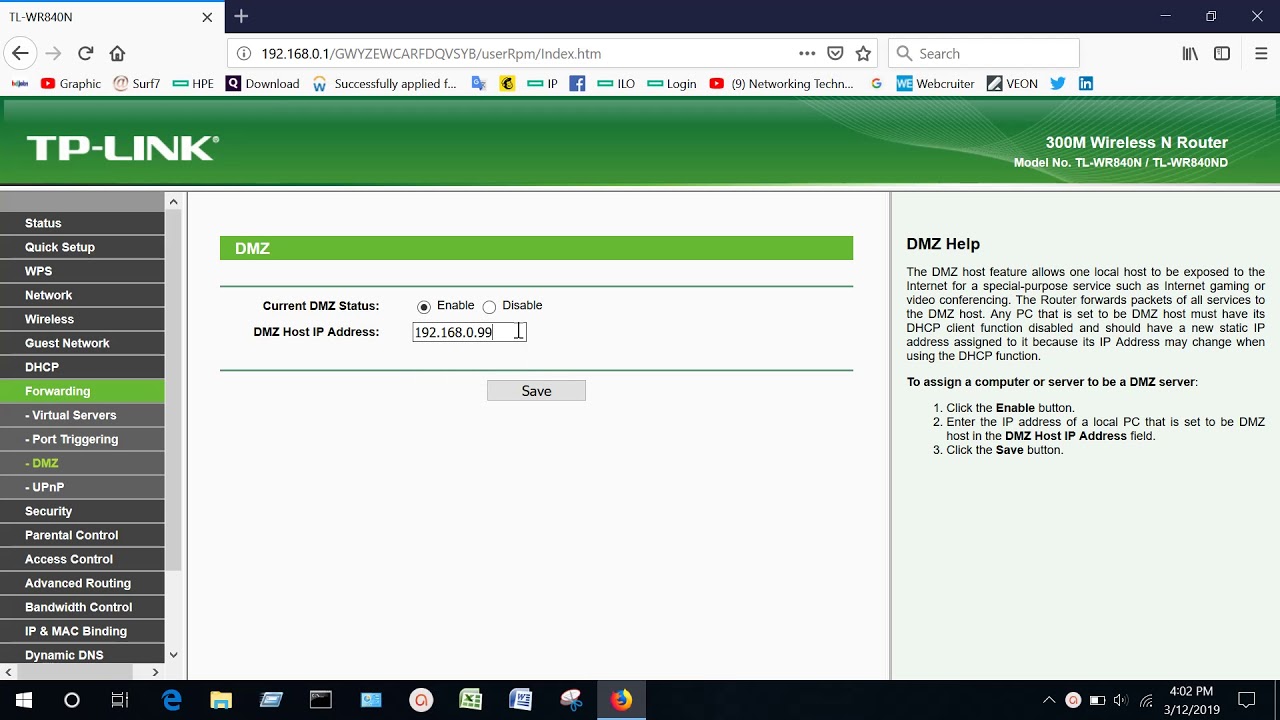
How To Setup DMZ demilitarized zone on a home router By TP Link Router

PPT - DNS & Mail in the DMZ PowerPoint Presentation, free download - ID

Screened Subnet Architectures (Building Internet Firewalls, 2nd Edition)

Designing and Using DMZ Networks to Protect Internet Servers | Linux
